When you hear the name "Pam Adkisson," it's natural to wonder about the person behind it, perhaps seeking a biography or insights into their work. However, our discussion today, drawing solely from the information at hand, takes a slightly different turn. While the specific name "Pam Adkisson" doesn't appear in the details we have, we do find a very important concept abbreviated as "PAM," alongside a mention of "Pam Bondi." This article aims to clarify what "PAM" truly stands for in a crucial context, and touch upon the only "Pam" figure referenced in our source material.
You see, the world of digital safety is always changing, and one very key part of keeping things secure is something called Privileged Access Management, often just called PAM. It's a system, more or less, that helps protect a company's most important digital bits. This is about making sure only the right people, and just the right systems, can get to the really sensitive stuff. It's a bit like having a very strict bouncer at the most exclusive club, always checking credentials.
So, while you might be looking for information on "Pam Adkisson," we'll actually be exploring the critical role of PAM in cybersecurity, and how it helps keep organizations safe. We'll also briefly look at the context where a "Pam" figure, specifically Pam Bondi, is mentioned in our text. It's quite interesting, actually, how these different pieces come together, even if not directly linked to the initial name you might have searched for.
Table of Contents
What is Privileged Access Management (PAM)?
Privileged Access Management, or PAM, is that kind of identity security solution, really. It's a way, you know, for groups to keep themselves safe from digital dangers. This system, it basically helps by watching things closely. It's almost like a watchful eye, always looking for anything out of place. It can spot issues early, which is pretty important, actually. And then, it stops things that aren't supposed to happen, keeping unauthorized actions from taking hold. This makes a big difference, you see, in protecting a company's valuable information.
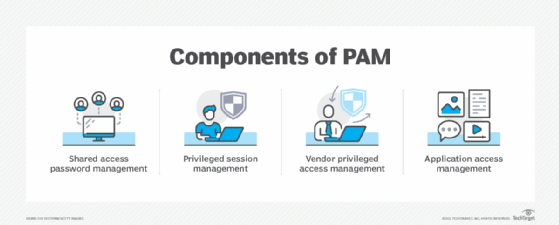
PAM, in a way, is made up of cybersecurity plans and special digital tools. These are all about having firm control over who gets "elevated" access or special permissions. This means, essentially, managing who has the keys to the most important parts of a system. It's not just about people, but also about other digital identities that might need to get to sensitive areas. This control is quite important, as it limits who can do what, and where, which is a good thing for security.
More or less, PAM is a type of identity management, and it's also a part of cybersecurity. Its main aim is to control, watch over, and keep safe those very special "privileged accounts." These are the accounts that have a lot of power within a system, so they need extra care. It's kind of like making sure the master key to a building is always accounted for and only used by those who absolutely need it. This focus helps prevent big problems before they even start, which is truly helpful.
PAM as an Identity Security Solution
So, PAM is often described as an identity security solution, and for good reason. It helps protect organizations from all sorts of digital threats. This protection comes from its ability to monitor what's happening, spot anything suspicious, and then prevent actions that aren't allowed. It's almost like having a very smart guard dog for your digital assets. This system helps keep things running smoothly and safely, which is, you know, quite important for any business these days. It gives peace of mind, basically.
When we talk about monitoring, PAM is constantly observing who is trying to access what, and how they are doing it. This watchful eye helps catch unusual patterns or attempts that might signal a problem. Then, there's the detecting part. If something looks off, the system is designed to flag it immediately. It's a bit like an alarm going off if someone tries to open a locked door without the right key. This quick detection is a crucial step in stopping bad actors, as a matter of fact.
And finally, the preventing aspect of PAM is really where it shines. It's not just about seeing a problem, but actively stopping unauthorized access or actions before they can cause harm. This could mean blocking a login attempt, or perhaps, limiting what a user can do once they're in. It's about putting up strong barriers to keep cyberthreats out. This proactive approach helps keep an organization's digital doors locked tight, which is, you know, a very good thing.
Strategies and Technologies in PAM
Privileged Access Management involves a mix of smart strategies and helpful technologies. These work together to give organizations firm control over who has elevated access and permissions. It’s not just about buying a piece of software; it’s about having a thoughtful plan for how to manage these powerful digital keys. This combination helps ensure that access is granted wisely and used properly, which is, well, pretty important.
The strategies often include setting up clear rules about who gets privileged access, when they can use it, and for how long. It’s about creating a framework, in a way, that guides how these powerful accounts are managed. For example, a strategy might be to require a second person to approve any high-level access request. This adds an extra layer of safety, you see, making it harder for unauthorized actions to occur. It’s all about careful planning, basically.
Then there are the technologies. These are the tools that put those strategies into action. They can include things like secure password vaults, which keep privileged account passwords safe and rotate them automatically. There are also session monitoring tools that record what a privileged user does while logged in. This helps with accountability, more or less. These technologies are what allow the strategies to be effective, providing the means to enforce the rules and keep things secure, which is quite useful.
Controlling, Monitoring, and Protecting Accounts
PAM is very focused on the control, monitoring, and protection of privileged accounts. These are the accounts with special, elevated permissions, like those used by system administrators or for critical applications. Controlling these accounts means making sure only authorized people can use them, and only for approved tasks. It's about limiting the potential for misuse, which is, you know, a big part of security.
Monitoring is another key piece of the puzzle. This involves constantly watching what these privileged accounts are doing. Are they accessing the right systems? Are they performing expected actions? This constant observation helps to quickly spot any unusual behavior that might indicate a security breach. It's a bit like having security cameras on your most valuable assets, always recording, just in case. This helps in understanding what happened if something goes wrong, which is, in fact, quite helpful.
And then, of course, there's the protection aspect. This means safeguarding the accounts themselves from being compromised. This could involve strong authentication methods, like multi-factor authentication, or automatically changing passwords after each use. The goal is to make it extremely difficult for an attacker to gain control of a privileged account. This protection is, arguably, the most vital part, as it forms the first line of defense against serious cyberthreats, you see.
Safeguarding Sensitive Data and Systems
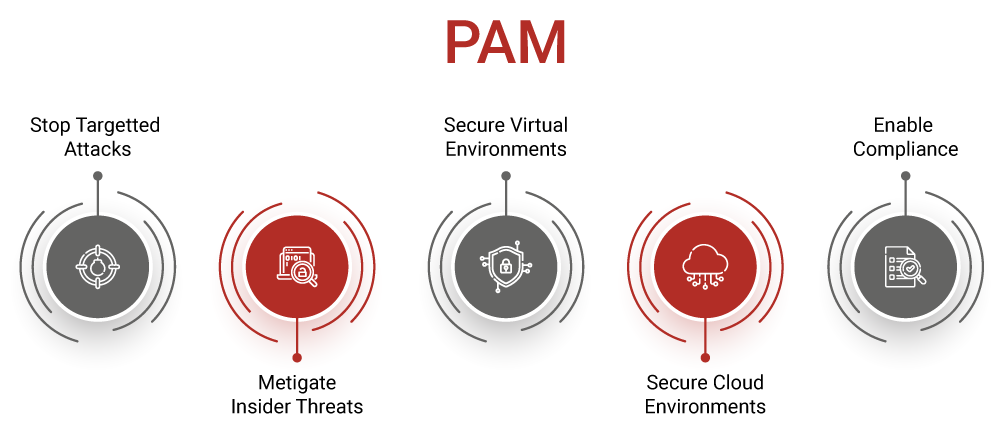
One of the main goals of PAM is to safeguard an organization's most sensitive data and critical systems. This means protecting information that, if exposed or tampered with, could cause significant harm. Think of customer records, financial data, or the very core systems that keep a business running. PAM is a cybersecurity strategy and a set of technologies specifically aimed at keeping these precious assets safe, which is pretty important for any group.
This safeguarding is done by meticulously controlling access to these sensitive areas. It's about ensuring that only those with a legitimate need can get in, and that their actions are carefully managed. For example, if a system holds highly confidential customer information, PAM would ensure that only specific, authorized personnel can view or modify it, and that their access is temporary or limited to exactly what they need to do. This level of control helps prevent accidental or malicious data breaches, which is, you know, a big concern for everyone.
The critical systems themselves, like servers or network infrastructure, are also a major focus. These are the backbone of any digital operation. PAM helps protect them by managing who can log into them with administrative rights, and what commands they can run. This prevents unauthorized changes or shutdowns that could disrupt services. It’s about keeping the lights on, basically, and making sure everything works as it should, which is, well, quite essential for operations.
Managing and Securing Critical Access
Privileged Access Management helps organizations manage and secure access to their most critical systems, applications, and data. These are the resources that are typically reserved for those special, privileged accounts. It's about making sure that the keys to the kingdom are not just lying around for anyone to pick up. This kind of careful management is crucial for keeping an organization's digital environment sound, which is, you know, a constant challenge.
The "manage" part involves knowing exactly who has access to what, when they used it, and why. It's about having a clear picture of all privileged access points. This includes not just human users, but also automated processes or applications that might need high-level permissions to function. Having this visibility helps an organization keep track of its digital footprint, which is, actually, a good practice for security.
Then comes the "secure" aspect. This means putting strong protections in place around these critical access points. It's about making it very difficult for unauthorized individuals to gain control of a privileged account or to misuse one. This could involve advanced authentication methods, or even automatically removing access once a task is completed. The goal is to minimize the window of opportunity for attackers, which is, more or less, the core of good cybersecurity, you see.
Identifying Needs and Setting Policies
Privileged Access Management identifies the people, processes, and technology that truly need privileged access. This is a very important first step, as you can't protect what you don't know about. It’s about figuring out who really needs those special permissions to do their job, and what systems or automated tasks require them. This clear understanding helps to avoid giving out more access than is necessary, which is, you know, a common security mistake.
Once these needs are identified, PAM then helps specify policies to secure sensitive resources within an organization. These policies are like the rules of the road for privileged access. They dictate how access is granted, how it's used, and how it's monitored. For instance, a policy might state that all privileged sessions must be recorded, or that passwords for these accounts must be changed every day. These rules are very important, as they provide a framework for safe operations, basically.
These policies are not just written down; they are enforced by the PAM system itself. This means that the technology ensures that the rules are followed, preventing deviations that could create security weaknesses. It's about automating the security process as much as possible, which is quite efficient. This combination of identifying needs and setting strict, enforced policies is what makes PAM such a powerful tool for protecting an organization's most valuable digital assets, which is, well, pretty vital.
The Mention of Pam Bondi
Our source text also includes a brief mention of a person named Pam Bondi. It states that Bondi's announcement came after a Wall Street Journal report. This report was about a letter that someone named Trump sent to Epstein back in 2003. This context gives us a glimpse into a specific public discussion she was involved in, which is, you know, part of her public record.
The text further notes that Pam Bondi was trying to move past questions about how she handled certain Justice Department files. These files were connected to the Jeffrey Epstein investigation. There was, apparently, growing pressure on her regarding this matter. This suggests a period of public scrutiny and discussion around her actions in that particular role. It's interesting, actually, how these public figures sometimes face such intense examination.
It's important to remember that our provided text gives us very limited information about Pam Bondi. It doesn't offer biographical details or a full account of her career, just these specific references to her involvement in a particular public issue. So, while the name "Pam" appears, it's in the context of these specific events and not a broader personal profile. This is, basically, all the information we have about any "Pam" figure from the text itself.
Frequently Asked Questions (FAQ)
What does PAM stand for in cybersecurity?
PAM stands for Privileged Access Management. It's a type of identity security solution that helps protect organizations from digital threats by managing and securing elevated access to critical systems and data. It's a key part of keeping digital information safe, you see, which is very important these days.
How does Privileged Access Management protect an organization?
PAM protects an organization by controlling, monitoring, and safeguarding privileged accounts. It identifies who or what needs special access, sets strict policies for its use, and then enforces those rules. This helps prevent unauthorized actions and keeps sensitive data secure, which is, you know, quite helpful.
Is "Pam Adkisson" related to Privileged Access Management or Pam Bondi?
Based solely on the text provided, the name "Pam Adkisson" is not mentioned in direct relation to Privileged Access Management (PAM) or Pam Bondi. The text discusses PAM as a cybersecurity concept and refers to "Pam Bondi" in the context of specific public events. So, there isn't a direct link from our information, actually.
For more information on digital security practices, you might want to learn more about cybersecurity solutions on our site. You can also find additional insights by exploring this page, which covers various aspects of keeping your digital world safe. Understanding these concepts is, you know, pretty essential for anyone in today's connected world, as a matter of fact.
The ongoing importance of robust security measures, particularly those like Privileged Access Management, cannot be overstated. As digital landscapes continue to evolve, protecting an organization's most sensitive information and critical systems remains a top priority. It's about building strong defenses against ever-present threats, which is, you know, a continuous effort for everyone involved in keeping data safe.